One of the most concerning errors your site visitors can encounter is a security warning. With all of the brute force attacks, malware, and denial of service attacks, it’s critically important for internet users to browse and shop securely. If your site is displaying the ERR_SSL_OBSOLETE_VERSION warning, visitors won’t be able to access your site without clicking on a link in the error that basically tells them that they shouldn’t return.
In this post, we’ll discuss what the ERR_SSL_OBSOLETE_VERSION warning is and what steps you can take to fix it. We’ll also show you how to test these fixes locally on the two most common web servers — Apache and NGINX. Let’s rock and roll.
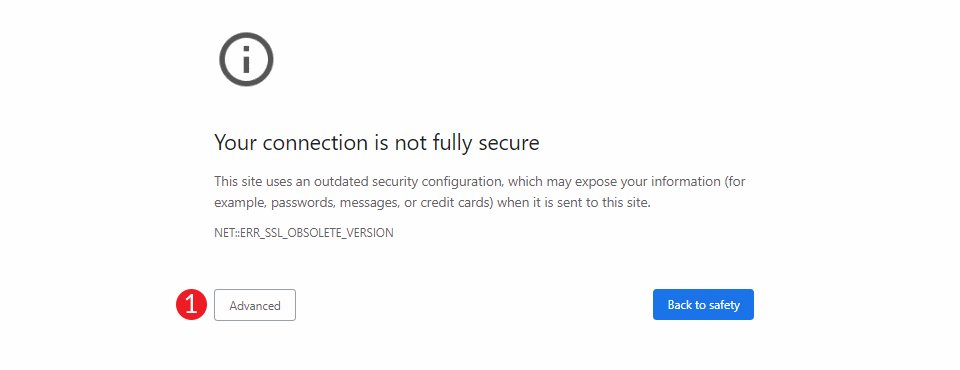
What is the ERR_SSL_OBSOLETE_VERSION Warning?
The ERR_SSL_OBSOLETE_VERSION warning is an error message your site visitors see if your security certificate is using an outdated version such as TLS 1.0 or 1.1. Beginning with the release of Chrome 72, those versions were no longer supported.
What is TLS vs SSL?
Transport Layer Security (TLS) is an internet security protocol that enables authentication and safe delivery of content on the internet. For example, it makes things like using a credit card for purchases or filling out employee applications with sensitive information on websites safe.
Secure Socket Layers (SSL) is a deprecated method of encrypting the connection between a client and a server that has been replaced by the new TLS method. The difference between TLS and SSL these days is really only a matter of terminology. Most people still use the term SSL even though TLS is the actual protocol being used.
Why Should You Care About TLS if you have an SSL?
As previously mentioned, your site is technically not using SSL anymore anyway. Generally speaking, all SSL certificates are actually TLS certificates these days. Most hosting providers still use the term SSL certificate because of the notoriety it brings, but use TLS for its security and speed advantages.
How Updating Your Server’s TLS Version Can Fix ERR_SSL_OBSOLETE_VERSION
In 2019, Google announced that they would be discontinuing TLS 1.0 and 1.1 on Chrome because of their security vulnerabilities. Since the release of TLS 1.3 in 2018, Chrome has required at least version 1.2 to display websites without a warning. As a result, all websites utilizing previous versions of TLS are slapped with an unsightly ERR_SSL_OBSOLETE_VERSION message. Using unsupported versions of TLS is dangerous — not only for your website but also for your visitors.
Most major browsers now support TLS 1.3 (IE excluded) and its the default for transport security for Google, Youtube, and Netflix since 2020, among others. Not only does TLS 1.3 offer higher levels of security, but it also transfers data much faster. For example, TLS 1.3 takes half the time to transfer data from your visitor’s browser to your server than TLS 1.2 does. In addition, other internet protocols such as HTTPS, SMTP, and POP3 (used for emails), are already utilizing newer versions of TLS. Even if you aren’t receiving a warning on your site, you should ensure that your site is running at least TLS version 1.2. The security of your website depends on it.
How to fix ERR_SSL_OBSOLETE_VERSION in Chrome
If you are already seeing this error in Chrome when trying to access your website, your site is more than likely running an outdated TLS version. Fixing this problem will require various different methods that depend ultimately on your specific hosting provider. However, a great place to start is to verify what version of TLS your site is running.
How To Find What Version of TLS Your Site is Running
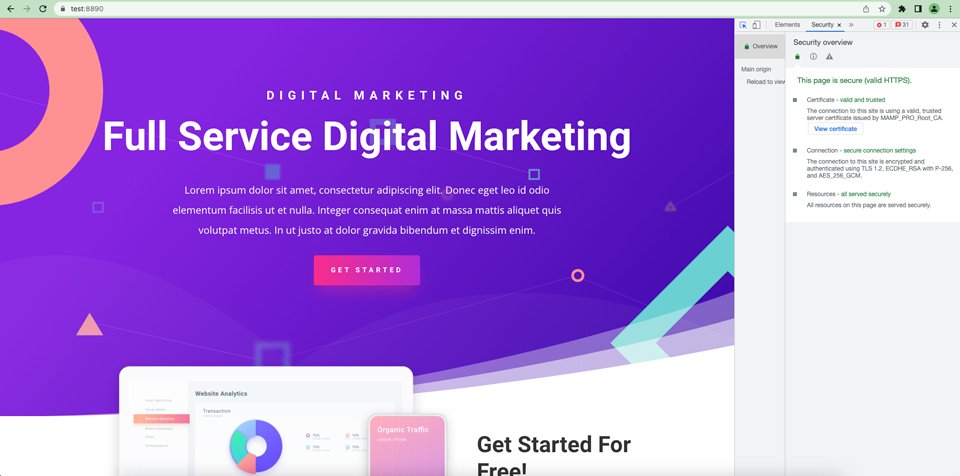
You can access this information in Chrome by using the dev tools and a keyboard shortcut. Press the Command+Option+C keys (on Mac) or Control+Shift+C (on Windows and Linux). Next, click on the security tab. The screen will pop up and reveal the version of TLS running on your site.
How To Find What Version of TLS Your Website Host/Server is Running
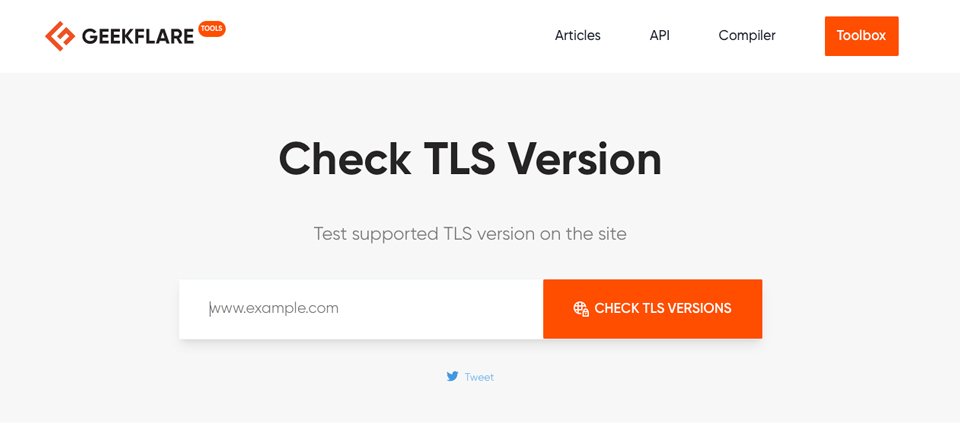
Before contacting your host or making any changes to your web host’s files, it’s a good idea to check to see if your host server supports TLS 1.2 or 1.3. You can accomplish this by visiting Geekflare’s TLS checker. Type in your host’s URL and click submit. When the results appear, scroll down until you see protocols installed. Look for TLS 1.2 and 1.3. If they are supported, you’ll see yes next to each.
Contact or Update Your Hosting Provider
Once you have verified that your site and/or server is running an outdated TLS version, the most simple solution to the ERR_SSL_OBSOLETE_VERSION error is to reach out to your hosting provider to determine if your version of TLS can be upgraded. Switching from TLS 1.0 or 1.1 to TLS 1.2+ would fix your problem. If that isn’t an option, it’s time to start researching a new host for your site.
We conducted tests on several top hosting providers to test their server’s capability for running TLS 1.3. Siteground, WP Engine, Pressable, Flywheel, Bluehost, and Cloudways all support it. So, if you host with any of these providers, chances are you won’t see the ERR_SSL_OBSOLETE_VERSION error. However, we should note that just because a hosting provider may support the most current TLS version, that doesn’t mean they are actually running it. Some web hosts still use 1.1 by default, which isn’t great. That’s why it’s important to check which version is currently installed on your site.
Testing a Fix to the ERR_SSL_OBSOLETE_VERSION Error on a Local Server
If you want to verify that updating the TLS version will fix the ERR_SSL_OBSOLETE_VERSION error for your website, you can always test it using a local server.
If you’re running WordPress, your hosting provider most likely uses Apache or NGINX web servers. For the purpose of this tutorial, we’ll be using a local server and MAMP Pro to edit our SSLProtocol files on Apache and NGINX to disable TLS 1.0 and 1.1. Next, we’ll enable support for TLS 1.2 and 1.3. If you are using a Windows machine, you can follow along with us using WAMP to accomplish the same task.
We’d like to reiterate that you check with your host to confirm that they support TLS 1.2 or 1.3. Making changes to your SSLProtocols without the proper support will result in breaking your SSL certificate.
How to Update TSL Version in Apache Using Mamp Pro
If you’re using MAMP Pro for this tutorial, we’ll assume you are already familiar with how to create a WordPress site and install an SSL. If you need some direction on how to do this, check out our Ultimate Guide to MAMP Pro for WordPress Users.
How Disable TLS 1.0 and 1.1 in Apache
In order to disable TLS 1.0 and 1.1 in Apache, you’ll need to edit the configuration file that contains the SSLProtocol for your web server. Depending on the platform you are using, this file could be located in different places.
On a default Apache location, it’s likely to be located here:
/usr/local/apache2/conf/extra/httpd-ssl.conf
If you are running an Ubuntu/Debian server, the file will likely be found here:
/etc/apache2/mods-enabled/ssl.conf
Finally, if you are running a local server on macOS via MAMP Pro (as we are), you’ll find the file here:
/mamp/conf/apache/extra/httpd-ssl.conf
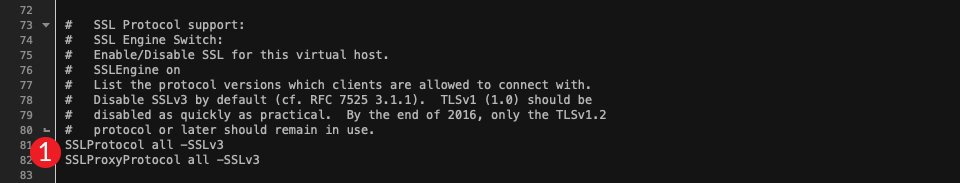
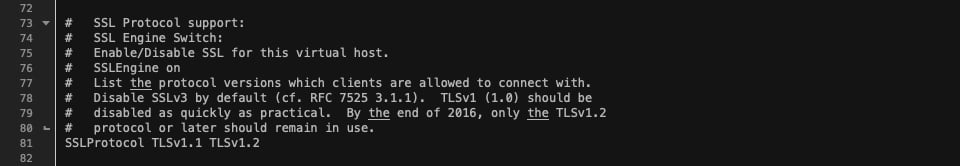
Next, look for the SSL Protocol Support section, which will consist of a few lines of code. This is the default setting of your httpd-ssl.conf file:
To determine what protocols are enabled, look at the last two lines of code.
We will need to tell Apache to only run versions of TLS 1.2 or above. Right now, all versions are enabled. To change that, you’ll change SSLProtocol all -SSLv3 SSLProxyProtocol all -SSLv3 to the following:
SSLProtocol TLSv1.1 TLSv1.2
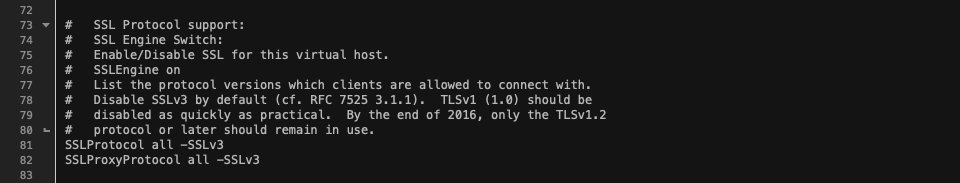
The file should now look like this:
The last step is to restart the server. Once the server restarts, open your website in an incognito window. The ERR_SSL_OBSOLETE_VERSION warning should be gone. Open your site and use the dev tools to view your security settings.
How to Update TLS Version in NGINX Using Mamp Pro
To update the SSLProtocol on an NGINX web server, you’ll need to locate your site’s configuration files. It could also be located in the primary NGINX configuration file, as in with MAMP Pro. To edit the file using MAMP, navigate to mamp/conf/nginx/nginx.conf. Open the file with your HTML/text editor. For this tutorial, we’re using BBedit, but any editor will do. If you aren’t following along using MAMP Pro, the nginx.conf file is usually located in /etc/nginx/nginx.conf.
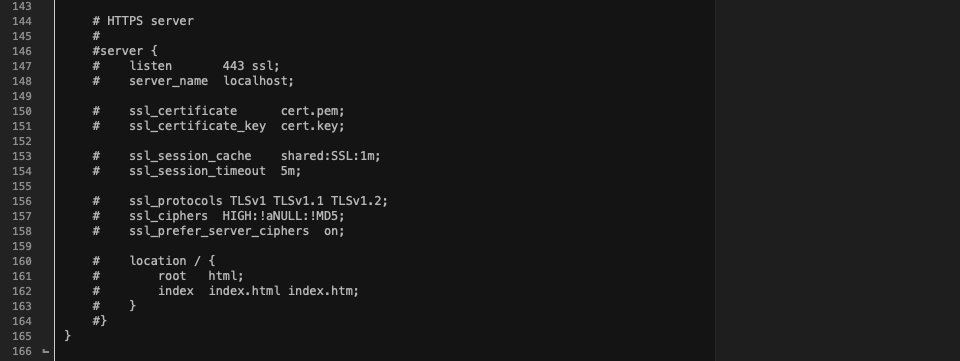
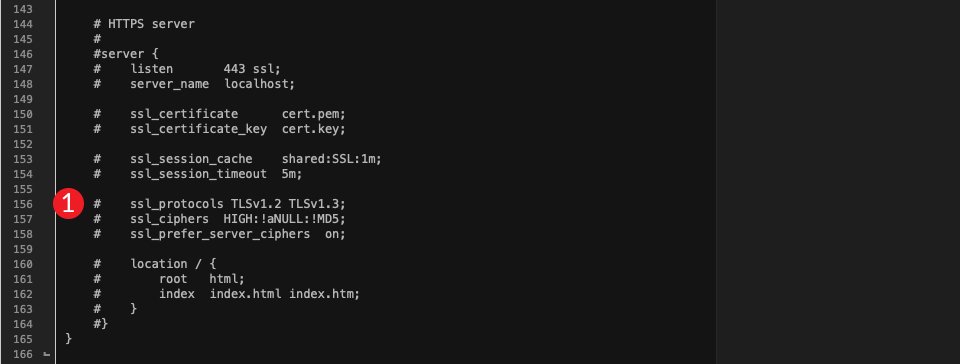
Scroll towards the bottom until you see the line beginning with ssl_protocols. If you have all TLS versions enabled, your file will look like this:
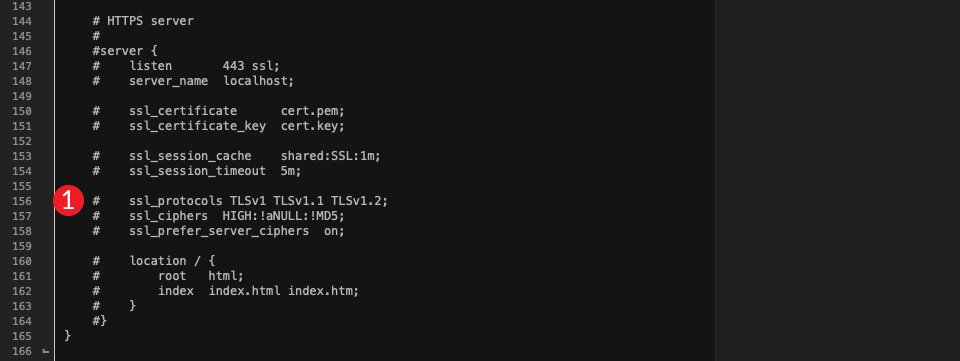
As you can see, TLS 1.0, 1.1, and 1.2 are enabled, but there’s no support for 1.3. To change that, you’ll want to change ssl_protocols TLSv1 TLSv1.1 TLSv1.2; to the following:
ssl_protocols TLSv1.2 TLSv1.3;
The file should now look like this:
Your server should now only be using TLS versions 1.2 and 1.3. To confirm, restart your server and pull up your site in Chrome. Check your settings using the dev inspector tools. As previously mentioned, you can do this by pressing the Command+Option+C keys (on Mac) or Control+Shift+C (on Windows and Linux), then clicking on the security tab.
We’d like to mention that settings in your default configuration could be overwritten by an individual domain’s server block. If you have implemented our fix and are still getting the ERR_SSL_OBSOLETE_VERSION warning, that could be the root cause.
Wrapping Things Up
With security concerns growing at a rapid pace, it’s important to keep your site up to date with the latest versions of TLS. We know that browser errors can be a frustrating experience, especially if you don’t know what to do to fix them. You can confirm the issue using tools like Chrome Dev Tools and Geekflare’s TLS checker. But, unfortunately, the solution to the problem is updating the TLS version which can only be done at the server level. So the best thing to do is contact your host or, if needed, upgrade your hosting provider to make sure they support the new TLS versions. It also might be helpful to test newer versions of TLS on your site locally on Apache and NGINX web servers. This will help ensure that your visitors won’t be confronted with the unsightly ERR_SSL_OBSOLETE_VERSION warning when you do take those changes live.
Have you ever encountered the ERR_SSL_OBSOLETE_VERSION warning error in Chrome? If so, sound off in the comment section below.
Featured Image valeriya kozoriz, Funtap / shutterstock.com