[ad_1]
Many people hear the word hack and think of someone sitting in a dark basement in a hoodie, typing code into a command line, targeting a website by breaking through firewalls and dodging security bots like they’re a supervillain on the run until the site is broken and taken down from the internet. But that’s not the reality of it. In truth, a hack is generally malware that’s been slyly inserted into your website’s server by a bot that found a vulnerability of some kind. And beyond that, there is a good chance that if your website has been hacked (read: infected by hidden malware), you don’t even know it. But we’re here to help make sure you know how to clean it up with a WordPress malware scan.
Let’s get to it!
Subscribe To Our Youtube Channel
How Does Hidden Malware Get Installed?
Hackers can gain access to your site in a number of ways. One of the most common is known as a brute force attack, where a botnet tries various username/password combinations until one works and lets them in. Once they have access to your site, they can do what they want and install any malicious code they desire.
It might get installed from a file you downloaded to your local machine that contained malware that found its way to your server. You might have even (accidentally, of course) clicked a phishing link or been redirected by a compromised website to one that seemed legitimate.
There are even entire networks of bots that search the internet for WordPress websites with specific vulnerabilities. Like out-of-date plugins, themes with specific, unpatched exploits, servers that run old versions of PHP, and so on.
Having hidden malware on your site might mean that you have taken an action that caused its installation, but not always. These things happen to all of us at some point, and we want you not to beat yourself up too badly if it happens. Because while it’s definitely not a good occurrence, it’s fixable if you follow the right steps. Which we’re going to take you through now.
1. Choose Your Anti-Malware Protection Plugin
Whether or not you think you have hidden malware on your site, the first step is choosing anti-malware software. For WordPress users, two of the top choices are WordFence and Sucuri. Both of these are tried, tested, and trusted to protect WordPress sites. And both of them offer stellar free versions that tens of thousands of users trust, on top of the the more advanced premium versions.
You can’t really go wrong with either. But for this article, we’re going to use WordFence as an example.
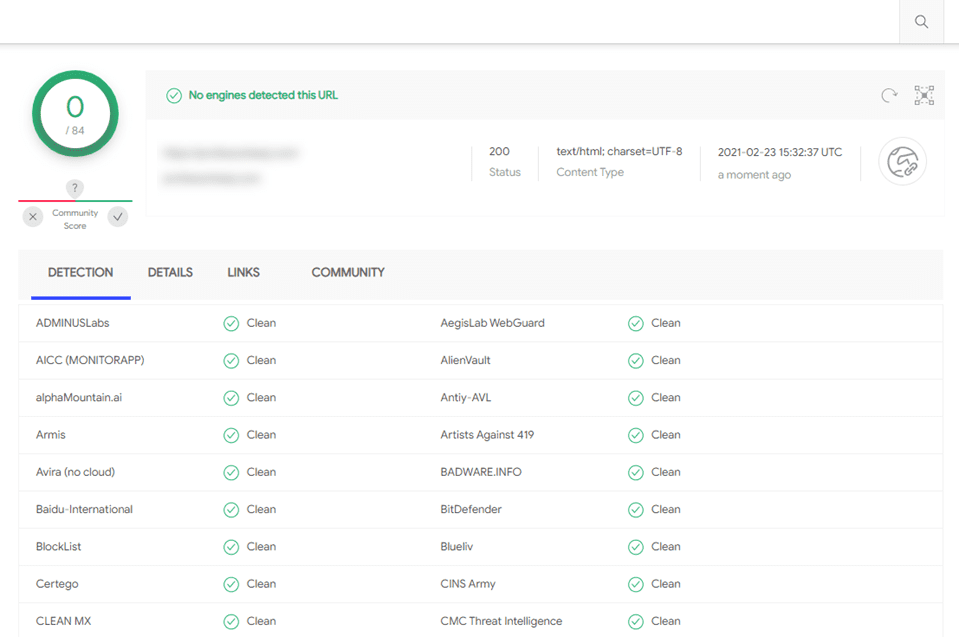
Additionally, you might choose some external URL checkers like VirusTotal.
These kinds of services run your URL and public files through various databases. These index URLs and indicate whether they’ve been tagged as compromised or suspicious. If you don’t come back clean, either WordFence or Sucuri can help you fix it in the following steps.
2. How to Scan Your Website For Malware
No matter what the external websites say, you will want to run a malware scan with a WordPress plugin so that it can go deep inside your file system. Like we said earlier, we will be using WordFence for this example. You can download it and install it from the WordPress.org repository.
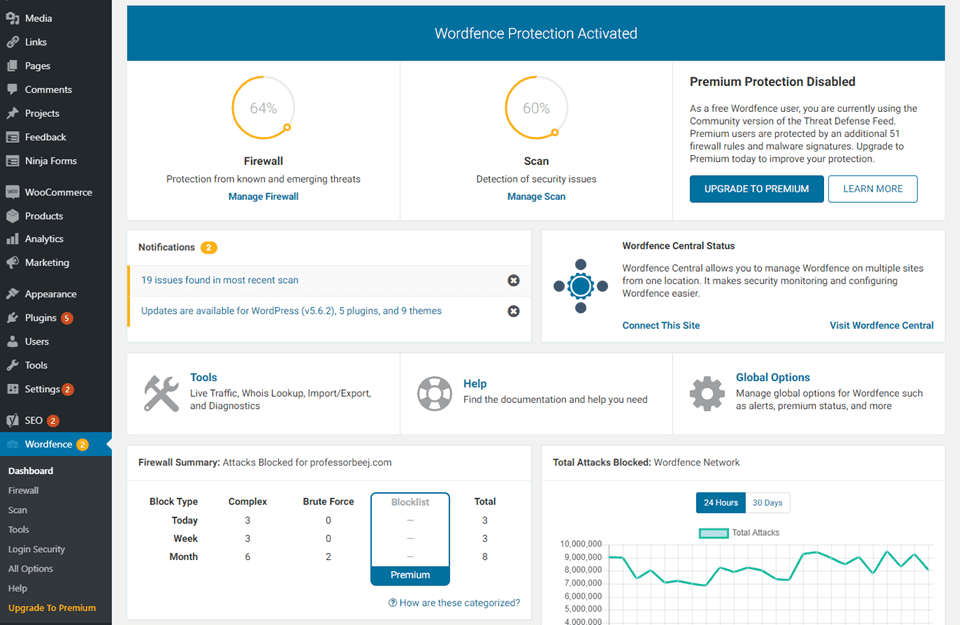
The standard WordFence dashboard that you see is pretty useful, and it appears under WordFence – Dashboard in your WP admin panel. You can see a summary of protection up to that point, the number of scans, the number of issues in the most recent scan, and more.
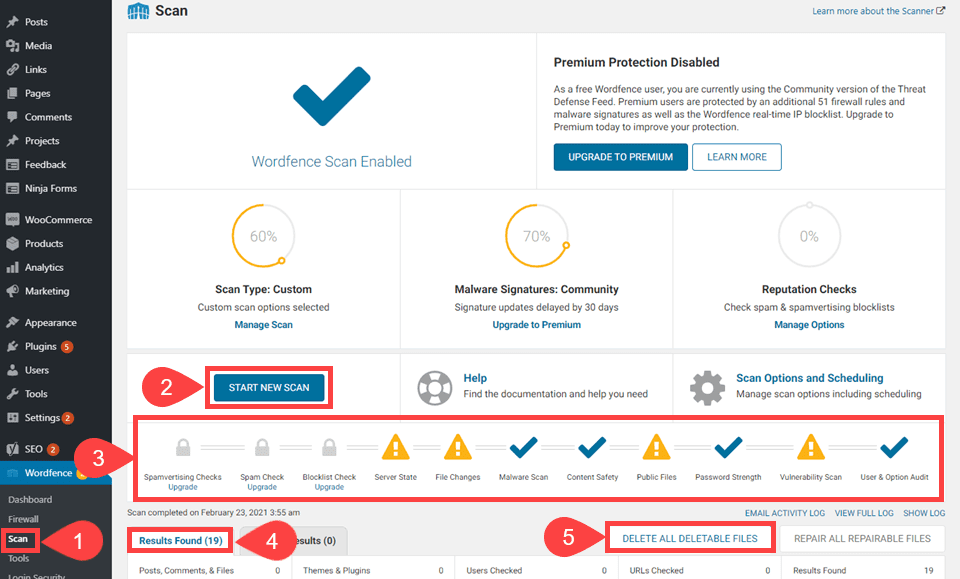
When you go into WordFence – Scan, you see a lot of data. But it’s easy to digest once you know what you’re looking at.
When you press the Start New Scan (2) button, WordFence works its way through a timeline (3) of various criteria. (We say timeline because it checks in this order.) After the scan, you see a detailed log of results in the Results Found (4) tab, and the actions you can take to the right (5).
3. How to Deal with Malware Scan Results
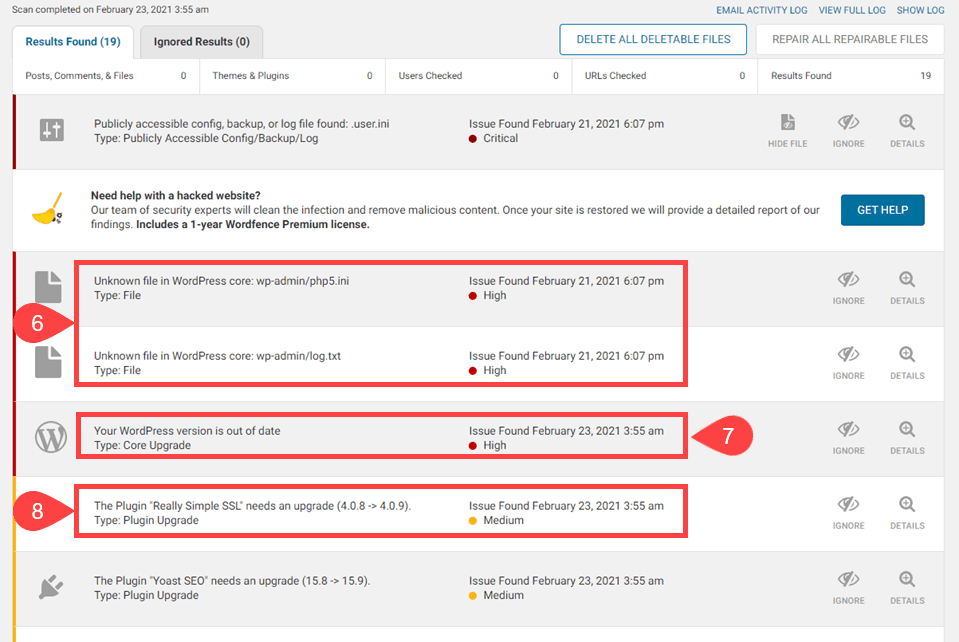
Once you see your results, it’s time to parse and take action on them. But even before that, you have to know what it’s saying.
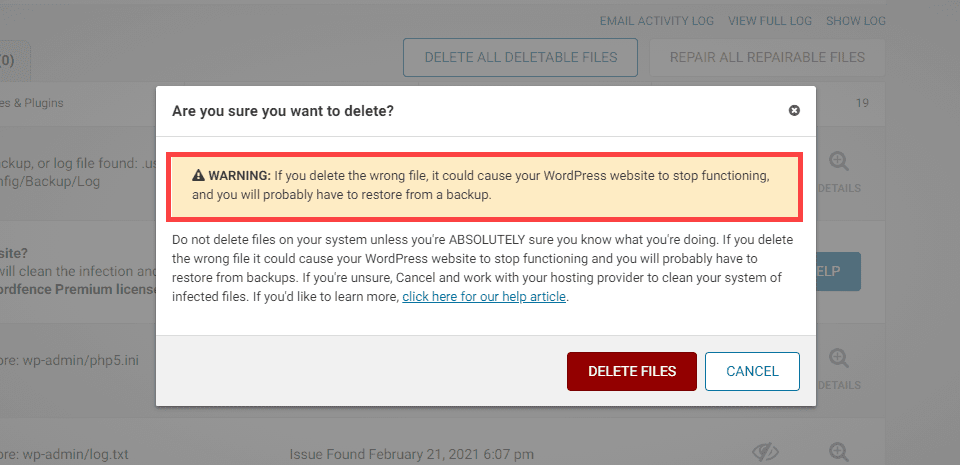
If you see a message labeled High Priority with a red dot (6), you need to take a look at it ASAP. Especially if you see it saying there is an unknown file in WordPress core. That is bad news. Luckily, WordFence lets you Delete All Deletable Files (5) with the click of a button.
You should always back up your site before doing that, however, just to make sure that you’re not removing anything necessary. WordFence even reminds you to do so.
Once that’s done and you press Delete Files to have WordFence take care of them. At this point, your site should be free of hidden malware. If you want to check even deeper, run a scan with Sucuri to see if it picks up anything WordFence misses. Additionally, you can subscribe to the premium version of either to get a deeper scan.
The malware-infected files are gone. So you only have to deal issues that are less pressing and most likely non-malware related. (Though they are just as important in their own ways).
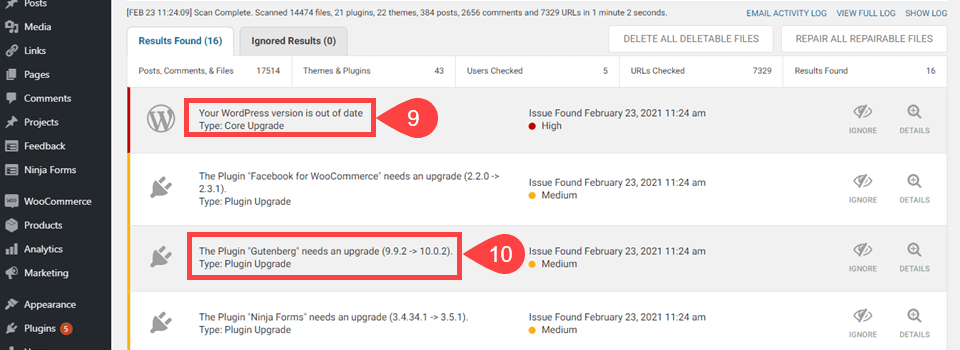
In this instance, the WordPress version is out of date (9). WordFence warns about it because outdated WP versions can contain severe security issues that haven’t been patched yet. If you’re out of date, then you’re a sitting duck for malware. Additionally, WordFence tells you about plugin and theme versions being out of date (10). For the exact same reason.
Note that the WP core update is marked High priority. The plugin updates are Medium. This is because in terms of WordPress website hacks, the people behind them are far more likely to target the core of the software that everyone uses. Not a single plugin or theme that only a handful use in comparison. It does happen, though, so it’s worth keeping an eye on.
4. What To Do After Finding Hidden Malware
It hurts to find malware on your site. It’s scary for you and for your customers and clients. After you clean your site and get the malware gone and shoo the hackers away, you can follow a few simple steps to shore up your defenses.
- Change all your passwords. You probably don’t know how the malware got there. But it’s possible and likely that your admin and user passwords were compromised in some way. So you need to change them all. Use this plugin to do it, and it will notify everyone at their registered email.
- Enable Two-Factor Authentication (2FA). By having 2FA enabled on your site, it means that even if a password is compromised, the attacker will unlikely be able to get further into your site. This step is becoming mandatory as attacks on WordPress sites increase.
- Audit Your Registered Users. Just to be safe, check the users on your site who have permission to edit files and permissions. If an attacker got inside your site and made their own user, 2FA and changing passwords will happen for them, too. So check to see if you have a mole and root them out. And by root them out, we mean delete that user and purge them from your database.
- Backup Your Site. Now that you are certain your website is clean, back it up. That way, you have a solid, sterile foundation to start from if anyone goes bananas again.
- Run Regular Malware Scans. Hopefully, you will keep WordFence or whatever security plugin you use installed. Set it to automatically scan your site and to email the results to you. The free version of WordFence will do this for you.
Wrapping Up with Scanning WordPress for Malware
Malware, hacking, viruses, brute force attacks…all of them are scary, but they’re all very manageable. You can handle any malicious code on your site by staying calm and running a few scans. The security professionals out there stay up to date on all the latest threats, so we can all trust them and their plugins to keep us, our machines, and our livelihoods safe. So with a quick install and button press, you can scan your WordPress site for malware and rest easy knowing your site is as clean as the day you installed it.
What are your experiences with having to scan WordPress for malware?
Article featured image by aurielaki / shutterstock.com
[ad_2]
Source link